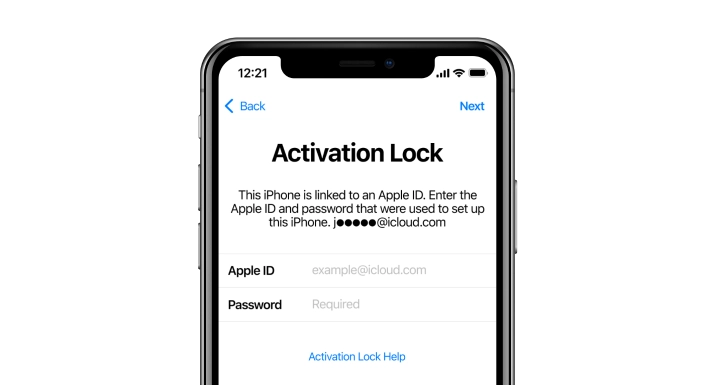
iCloud Activation Lock
Removal Tool.
The CheckM8 is the perfect solution for those in search of a straightforward and powerful tool that can remove Activation Lock from iCloud locked iPhone or iPad. With just one click, this tool can unlock your device and bypass the Activation Lock without any complications.
Attention
Supported iPhone Models:
A7+: from 5S up to iPhone X
A12+: from XR, XS, XS MAX up to iPhone 16 Pro Max
Supported iPad Models:
A7+: any iPad, iPad Pro, Air & Mini Up to 2019 models
A12+: any iPad, iPad Pro, Air & Mini From 2019 models onward
COMPATIBLE WITH:
-
- iPhone 5S → iPhone X
-
iOS versions: 12 - 16
Time Delivery: INSTANT
Supported on: Mac & Windows - iPhone XR/XS/XS Max → iPhone 16 Pro Max
-
iOS versions: 17.0.1 - 26.1
Time Delivery: Instant
Supported on: Mac & Windows
-
- iPads from 2013 to 2018 releases
-
iOS versions: 12 - 26.1
Time Delivery: INSTANT
Supported on: Mac & Windows - iPads from 2019 to 2025 releases
-
iOS versions: 17.0.1 - 26.1
Time Delivery: Instant
Supported on: Mac & Windows
-
- The software is compatible with macOS 10.11 or later and Windows 8, 10, 11
VIDEO PRESENTATION
Remove iCloud Activation Lock on iPhone and iPad.
Activation Lock Screen Removal on iPhone.
The CheckM8 tool enables the removal of Activation Lock on iPhones ranging from iPhone 5S to iPhone 15 Pro Max, including both GSM and CDMA (MEID) versions. It's one tool for the entire range of device models!
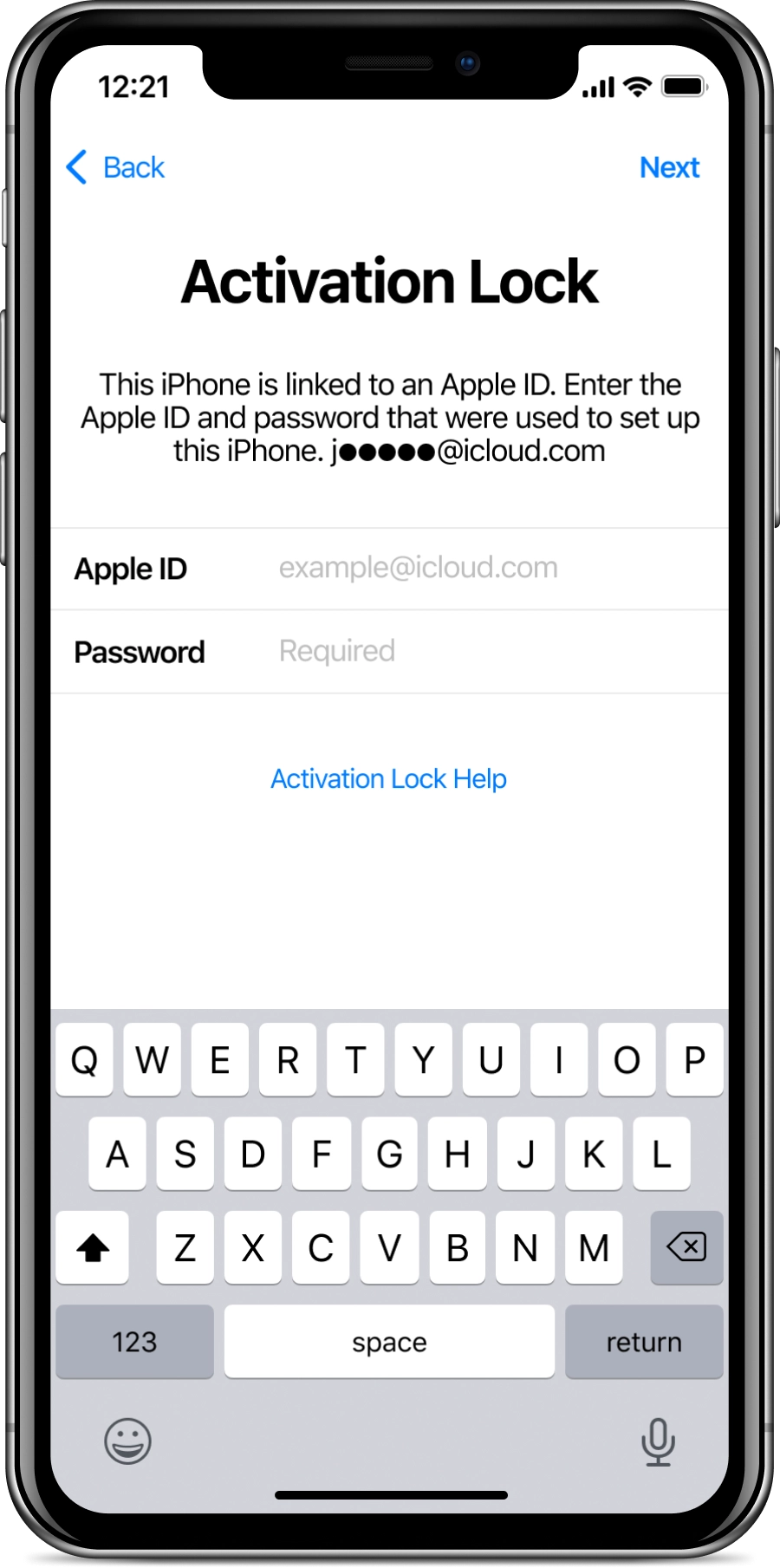
Thanks to the CheckM8 Tool, removing Activation Lock on iPhones has become extremely easy. The Checkm8 exploit used in the Checkra1n Jailbreak has been leveraged to develop the iCloud Removal Tool, which forms the core of the CheckM8 Tool.
It is not necessary to know the iCloud password as the program can bypass the activation step on a locked iPhone.
If you need to bypass iCloud on a device with an A12+ Bionic Apple CPU (including models such as iPhone XR, XS, XS Max, iPhone 11, 12, 13, 14, 15 and 16 series), please note that now it's an instant service.
Once your iPhone is unlocked, you can use it just like you normally would — make calls to your loved ones, use your Apple ID, listen to your favorite music, browse the internet, and play your favorite games. All limitations will be removed!
Please note: if you place a No Signal Bypass order, GSM networks and incoming/outgoing calls will not be available to you. However, all other functionality will remain enabled.
🗓 Devices verified before August 20, 2024 can still use Signal Bypass only
Activation Lock Screen Removal on iPad.
The CheckM8 supported iPad models equipments with processors between an A7 and an A12+. The WiFi and WiFi + Cellular models is supported!
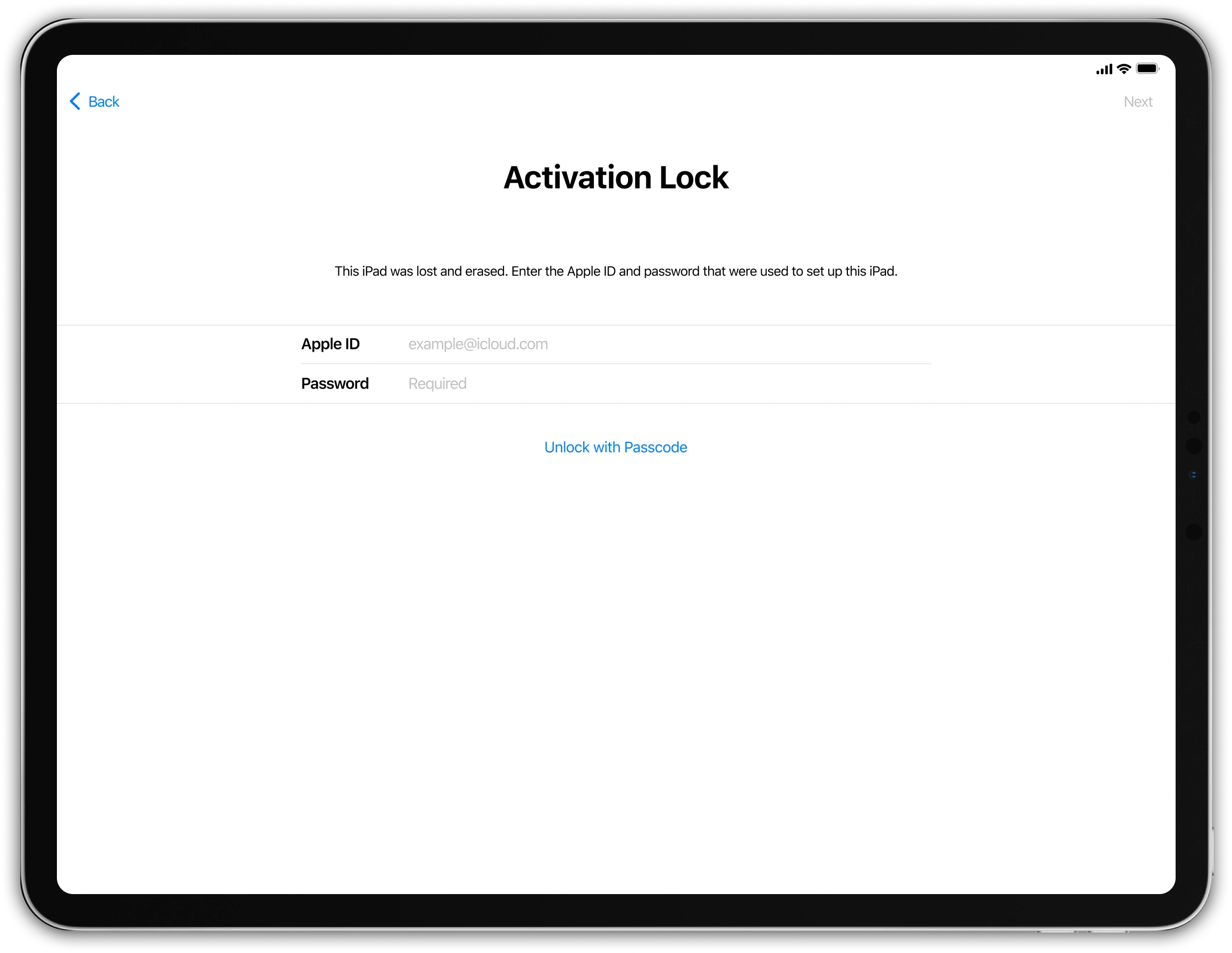
By using CheckM8, you can bypass any iPad models, including Wi-Fi and Wi-Fi + Cellular modes, covering releases from 2013 to 2024 on both Windows and macOS!
After the Activation Lock bypass process, the WiFi+Cellular models of iPads will be compatible with GSM networks.
Please note: if you place a No Signal Bypass order, GSM networks and incoming/outgoing calls will not be available to you. However, all other functionality will remain enabled.
🗓 Devices verified before August 20, 2024 can still use Signal Bypass only
Get iCloud Activation Lock Removal Tool.
RECENT SOFTWARE RELEASES
Software Updates.
Here you can find a list of the latest updates for CheckM8 iCloud Activation Lock Removal Tool. Do you want to be the first to know about new updates and discounts?
Join Telegram🗓 Devices verified before August 20, 2024 can still use Signal Bypass only
CheckM8 Reviews
How to Bypass Activation Lock using CheckM8 Software.
PLEASE NOTE:
The iCloud Bypass refers to a procedure that allows users to skip the Activation Lock on their iPhone or iPad. In essence, the bypass enables the device to bypass the activation step and recognize that it has already been activated.
- As a result, once you utilize the bypass to skip the Activation Lock, the device ought to function normally without any complications, except if you restore it to its factory settings.
If you employ the CheckM8 Activation Lock Bypass service, you have the benefit of reusing the software for free to bypass the Activation Lock on your iPhone or iPad anytime you require it again!
These are the instructions you will require:
-
Step 1.
Download & Install Software
Download the required version of the software for your computer running Windows or Mac OS.
If you are using macOS:
To begin the installation process, download the CheckM8 Tool for macOS and then proceed to right-click on the app icon. Next, left-click on 'Open' to initiate the process.
CheckM8.pkg' can't be opened
It's important to note that if you attempt to open an app by an identified developer that isn't registered with Apple, a warning message will appear, but this doesn't necessarily indicate that there's an issue with the app.
After finishing the installation process, you can open the CheckM8 app on your Mac by utilizing Launchpad.
If you are using Windows:
To initiate the installation process on a Windows operating system, first download the CheckM8 tool. Then, extract the downloaded package and proceed with the installation.
-
Step 2.
Verify if the device is eligible
Launch the installed tool and connect your iCloud-locked device to your computer using a Lightning cable.
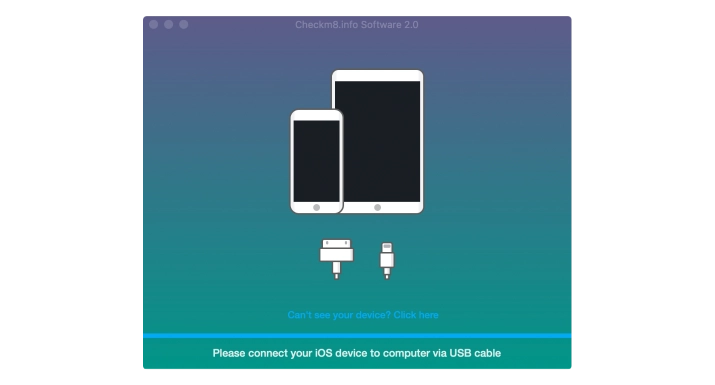
If you want to remove the Activation Lock on iPhone models from XS up to iPhone 16 Pro Max:
Attention!
✅ Connect your iPhone / iPad to a stable WI-FI network
⚡ Once on WI-FI → plug your device into a MacOS computer and run CheckM8 Software
🚀 Start the bypass process and enjoy full access!
🚫 Do NOT use a hotspot!
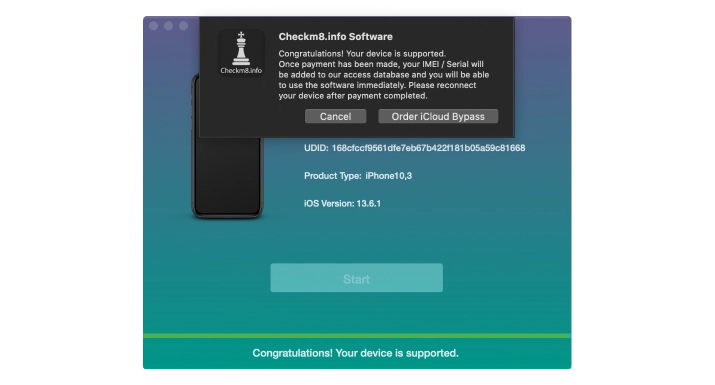
Connect your device and wait until the CheckM8 tool recognizes it and starts the verification process. If the process completes successfully, you will see a message about your iPhone's compatibility. The tool will then provide you with a link to the order page where you can get a Software License for your device.
Now you can proceed to the next step of this guide.
If you want to remove the Activation Lock on iPhone models from 5S up to X models or iPads with CPUs up to A11:
Attention!
To proceed with the process, you need to connect your iPhone or iPad to your Mac or Windows PC using a USB cable. If your Mac has only a Thunderbolt port, you will need to use a USB to Type-C adapter, otherwise, you may encounter an error (-20) with CheckRa1n.
To prevent incorrect orders, Checkm8 Software verifies your device after completing the jailbreaking process, which is integrated into the Checkra1n tool. To begin the process, just click on the 'Run' button.
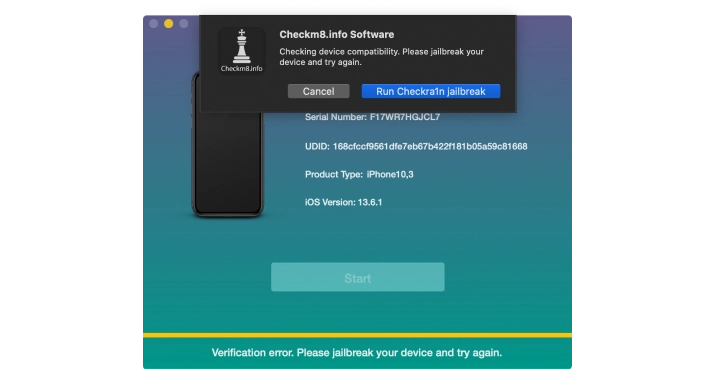
The jailbreak process begins when CheckRa1n detects a device in Recovery Mode that is connected to a Mac PC. Simply press the 'Start' button to proceed.
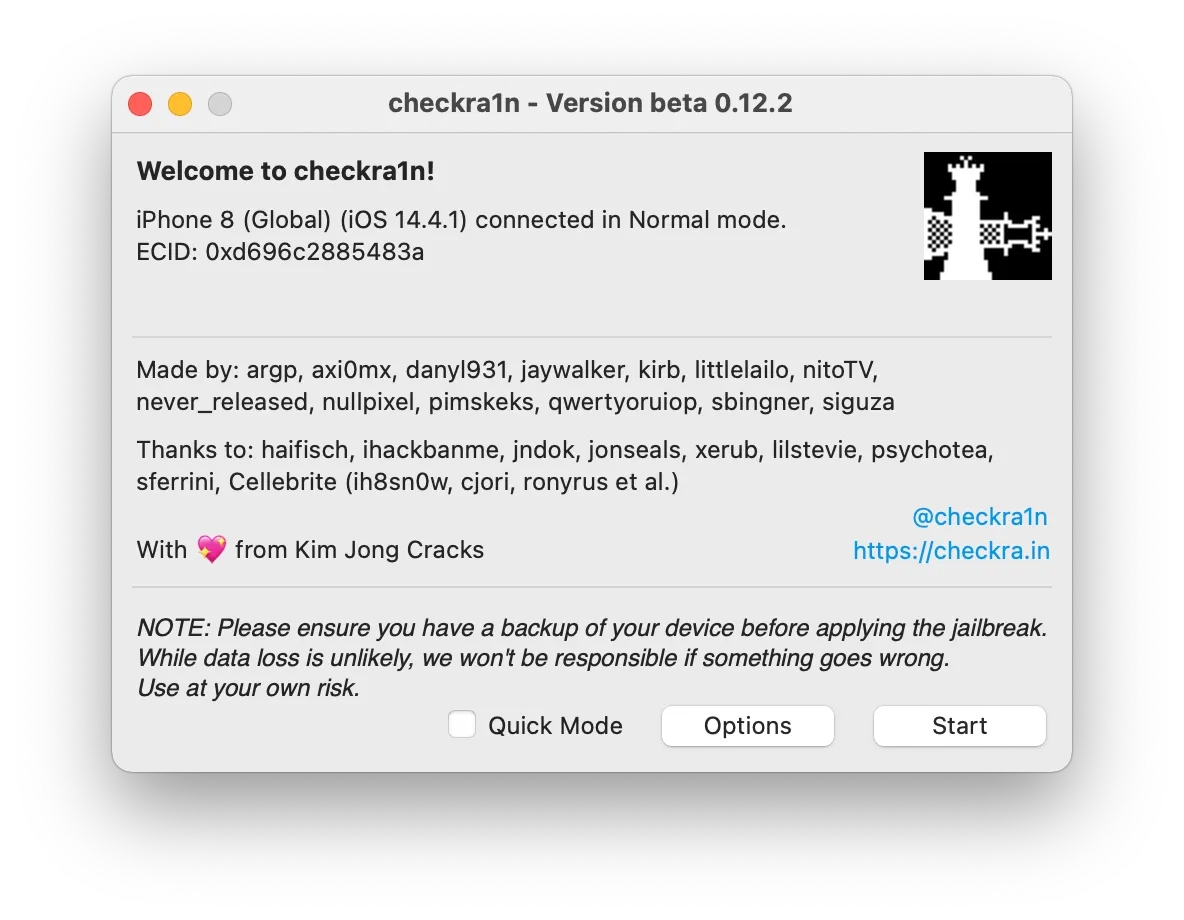
Enter the DFU mode on the device and adhere to the instructions displayed on the screen. Once the jailbreak process is complete, click on the 'Done' button.
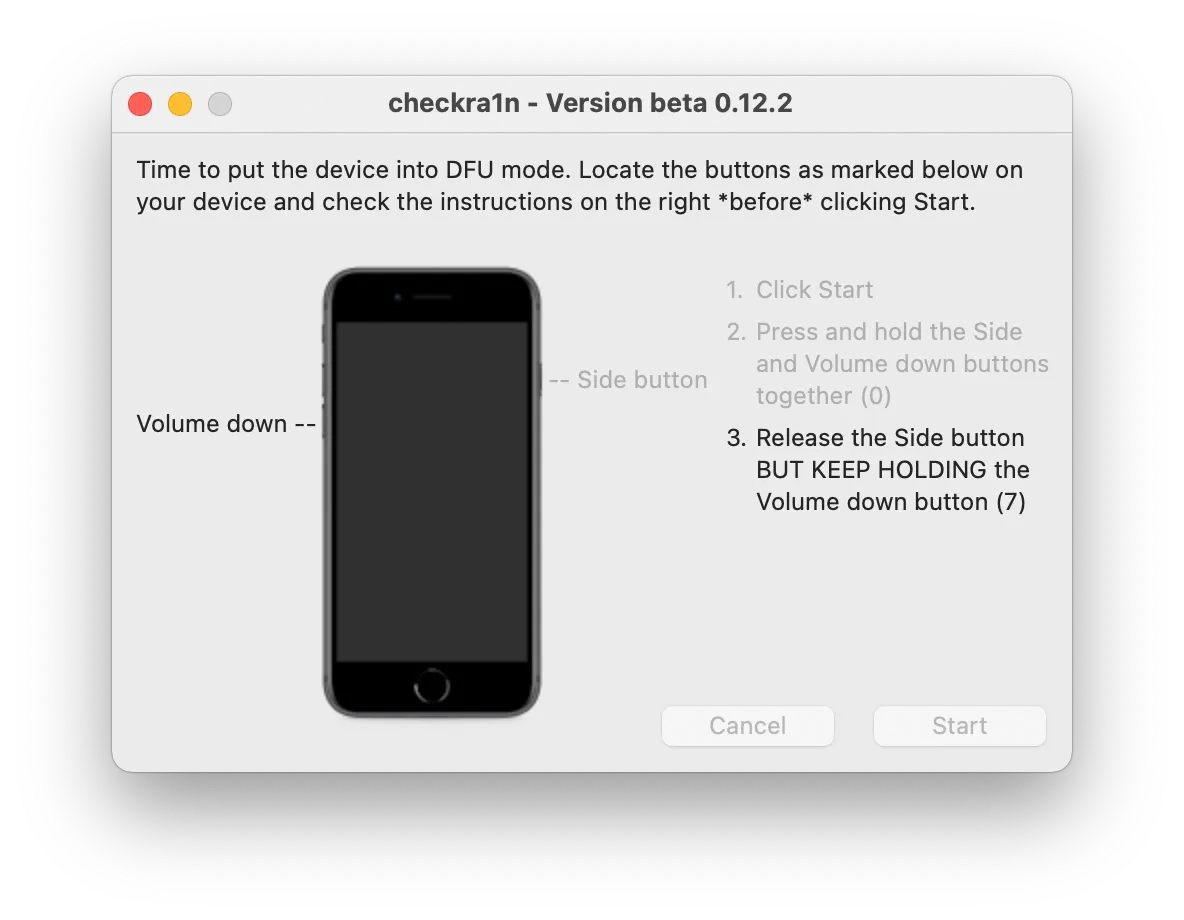
Upon recognizing your device, the CheckM8 tool will verify its compatibility.
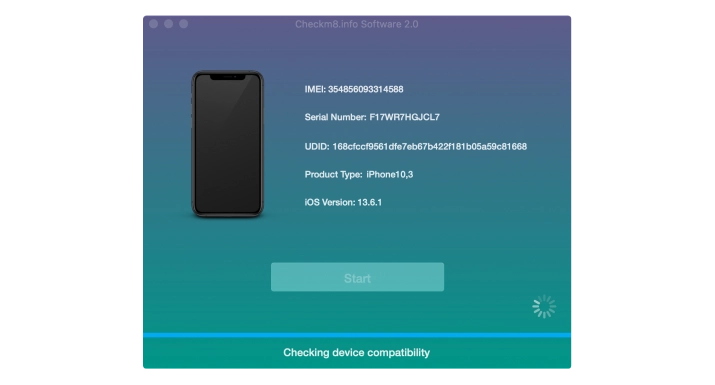
Once the compatibility is verified, the software will prompt you to purchase a license.
To proceed with payment, click on the "Order" button.
-
Step 3.
Order Service
On the payment page, you will find additional details about the service. The order form will automatically fill in information about your locked device, such as its IMEI or Serial Number. Enter your email address in the order form and proceed with the payment.
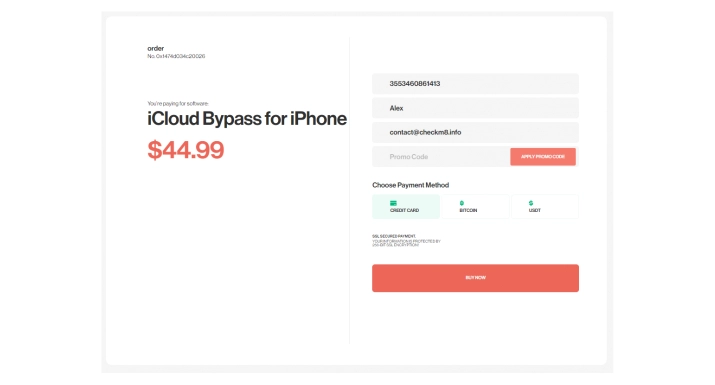
-
Step 4.
Bypass Activation Lock
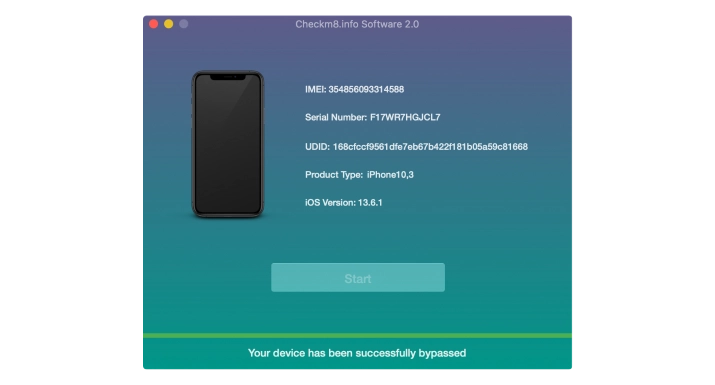
Once your payment has been cleared and Checkm8 Software recognizes your iCloud-locked iDevice, you will be given the option to bypass the iCloud Activation Lock Screen.
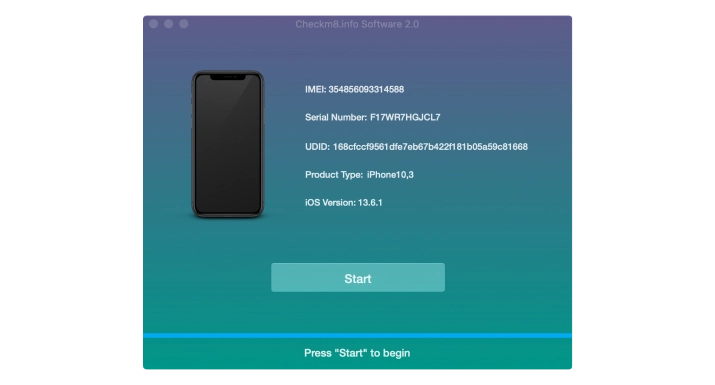
Simply click the "Start" button to initiate the process. It's important to keep your device connected to your Mac PC until you receive the notification that the unlocking process is complete.
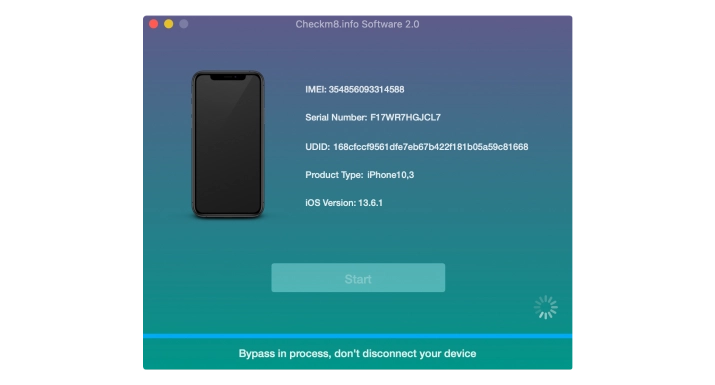

After successfully bypassing the activation on a locked device, it's advisable to set it up as new. Once set up, you can use your Apple ID to access all iCloud services, the Apple Store, and make incoming and outgoing calls as normal. You will receive full functionality of the device.
Download & Install Software
iCloud Activation Lock
Removal Service
Prices.
Please refer to the list of supported iPhone and iPad models for the Activation Lock bypass service. If your device is included in the list, you can utilize the tool to bypass iCloud on it.
-
- iPhone 16 Pro Max [No Signal]
$125
-
- iPhone 16 Pro [No Signal]
$120
-
- iPhone 16 Plus [No Signal]
$105
-
- iPhone 16 [No Signal]
$100
-
- iPhone 16e [No Signal]
$100
-
- iPhone 15 Pro Max
$150
-
- iPhone 15 Pro Max [No Signal]
$120
-
- iPhone 15 Pro
$115
-
- iPhone 15 Pro [No Signal]
$145
-
- iPhone 15 Plus
$130
-
- iPhone 15 Plus [No Signal]
$100
-
- iPhone 15
$125
-
- iPhone 15 [No Signal]
$95
-
- iPhone 14 Pro Max
$135
-
- iPhone 14 Pro Max [No Signal]
$105
-
- iPhone 14 Pro
$130
-
- iPhone 14 Pro [No Signal]
$100
-
- iPhone 14 Plus
$125
-
- iPhone 14 Plus [No Signal]
$95
-
- iPhone 14
$120
-
- iPhone 14 [No Signal]
$90
-
- iPhone 13 Pro Max
$125
-
- iPhone 13 Pro Max [No Signal]
$95
-
- iPhone 13 Pro
$115
-
- iPhone 13 Pro [No Signal]
$85
-
- iPhone 13
$110
-
- iPhone 13 [No Signal]
$80
-
- iPhone 13 Mini
$95
-
- iPhone 13 Mini [No Signal]
$65
-
- iPhone SE 3rd Gen
$95
-
- iPhone SE 3rd Gen [No Signal]
$65
-
- iPhone SE 2nd Gen
$95
-
- iPhone SE 2nd Gen [No Signal]
$65
-
- iPhone 13 Mini
$95
-
- iPhone 13 Mini [No Signal]
$65
-
- iPhone 12 Pro Max
$110
-
- iPhone 12 Pro Max [No Signal]
$80
-
- iPhone 12 Pro
$105
-
- iPhone 12 Pro [No Signal]
$75
-
- iPhone 12
$100
-
- iPhone 12 [No Signal]
$70
-
- iPhone 12 Mini
$95
-
- iPhone 12 Mini [No Signal]
$65
-
- iPhone 11 Pro Max
$105
-
- iPhone 11 Pro Max [No Signal]
$75
-
- iPhone 11 Pro
$100
-
- iPhone 11 Pro [No Signal]
$70
-
- iPhone 11
$95
-
- iPhone 11 [No Signal]
$65
-
- iPhone XR / XS/ XS MAX
$90
-
- iPhone XR / XS/ XS MAX [No Signal]
$60
-
- iPhone X
$39.99
-
- iPhone X [No Signal]
$19.99
-
- iPhone 8, 8Plus
$34.99
-
- iPhone 8, 8 Plus [No Signal]
$17.99
-
- iPhone 7, 7 Plus
$24.99
-
- iPhone 7, 7 Plus [No Signal]
$12.99
-
- iPhone 6S, 6S Plus, SE
$19.99
-
- iPhone 6S, 6S Plus, SE [No Signal]
$9.99
-
- iPhone 6, 6 Plus
$14.99
-
- iPhone 6, 6 Plus [No Signal]
$7.99
-
- iPhone 5S
$9.99
-
- iPhone 5S [No Signal]
$4.99
-
-
iPad 10.2-inch 8th Gen (Wi-Fi+Cellular) [NO SIGNAL]
$50
-
-
-
iPad Air 3rd Gen (Wi-Fi+Cellular) A12 [NO SIGNAL]
$50
-
-
-
iPad Mini 5th Gen (Wi-Fi+Cellular) [NO SIGNAL]
$50
-
-
-
iPad Pro 11-inch 3rd Gen (Wi-Fi+Cellular) M1 [NO SIGNAL]
$75
-
-
-
iPad Pro 12.9-inch 5th Gen (Wi-Fi+Cellular) M1 [NO SIGNAL]
$105
-
-
-
iCloud Bypass iPad Pro 12.9-inch 3rd Gen (Wi-Fi+Cellular) A12X [NO SIGNAL]
$75
-
-
-
iPad Pro 12.9-inch 3rd Gen 1TB (Wi-Fi+Cellular) A12X [NO SIGNAL]
$80
-
-
-
iPad Pro 11-inch 4th Gen (Wi-Fi+Cellular) M2 [NO SIGNAL]
$105
-
-
-
iPad Pro 12.9-inch 4th Gen (Wi-Fi+Cellular) A12Z [NO SIGNAL]
$85
-
-
-
iPad 10.2-inch 9th Gen (Wi-Fi+Cellular) A13 [NO SIGNAL]
$55
-
-
-
iPad Air 4th Gen (Wi-Fi+Cellular) A14 [NO SIGNAL]
$55
-
-
-
iPad 10.9-inch 10th Gen (Wi-Fi+Cellular) A14 [NO SIGNAL]
$55
-
-
-
iPad Mini 6th Gen (Wi-Fi+Cellular) A15 [NO SIGNAL]
$55
-
-
-
iPad Air 5th Gen (Wi-Fi+Cellular) M1 [NO SIGNAL]
$75
-
-
-
iPad Pro 12.9-inch 6th Gen (Wi-Fi+Cellular) M2 [NO SIGNAL]
$110
-
-
-
iPad Air 11-inch (Wi-Fi+Cellular) M2 [NO SIGNAL]
$115
-
-
-
iPad Air 13-inch (Wi-Fi+Cellular) M2 [NO SIGNAL]
$120
-
-
-
iPad Pro 11-inch (Wi-Fi+Cellular) M4 [NO SIGNAL]
$170
-
-
-
iPad Pro 13-inch (Wi-Fi+Cellular) M4 [NO SIGNAL]
$190
-
-
-
iPad Pro 11-inch 2nd Gen (Wi-Fi+Cellular) A12Z [NO SIGNAL]
$65
-
-
-
iPad Pro 11" (Wi-Fi+Cellular) [NO SIGNAL]
$55
-
-
-
iPad Pro 11" (Wi-Fi+Cellular) 1TB [NO SIGNAL]
$60
-
-
-
iPad Air 11" M3 (Wi-Fi+Cellular) [NO SIGNAL]
$130
-
-
-
iPad Air 13" M3 (Wi-Fi+Cellular) [NO SIGNAL]
$140
-
-
-
iPad 11th Gen A16 (Wi-Fi+Cellular) [NO SIGNAL]
$150
-
-
-
iPad Mini 7th Gen (A17 Pro) (Wi-Fi+Cellular) [NO SIGNAL]
$160
-
-
-
iPad up to 2017 (WiFi + Cellular)
$24.99
-
-
-
iPad up to 2017 (WiFi + Cellular) [No Signal]
$14.99
-
-
-
iPad up to 2017 (WiFi)
$14.99
-
-
-
iPad models 2017 - 2018 (WiFi + Cellular)
$34.99
-
-
-
iPad models 2017 - 2018 (WiFi + Cellular) [No Signal]
$24.99
-
-
-
iPad models 2017 - 2018 (WiFi)
$24.99
-
No Signal Version
iCloud Activation Lock
Removal Service
No Signal Version
After completing the iCloud Activation Lock bypass on iPhone or iPad models with the No Signal version, the device will function without cellular signal capabilities. This means it will operate like a WiFi-only device: you can connect to WiFi networks, use apps, browse the web, and make VOIP calls, but standard cellular functions like phone calls and SMS will not be available.
Tools for unlocking iPhone and iPad.
-
iCloud Activation Lock Removal Tool
Price from $15.99
This tool is used to get rid of the iCloud Activation Lock from iPhone and iPad devices running on iOS up to version 18
Discover SoftwarePrice from $15.99
-
![Remote Management [MDM] Bypass Tool](https://checkm8.info/new/img/service/remote-management-iphone-unlock.webp)
Remote Management [MDM] Bypass Tool
Price from $44.99
This software allows you to bypass the Mobile Device Management (MDM) Configuration Profile and remove the MDM lock screen on any iPhone and iPad model
Discover SoftwarePrice from $44.99
-
Open Menu FMI iCloud Unlock
From $14.99
This tool is made for iPhones and iPads that are not stuck on the Activation Lock screen, but instead are fully working devices with access to Media & Purchases menu
Discover SoftwarePrice from $14.99
Tools for unlocking Mac Computers.
-
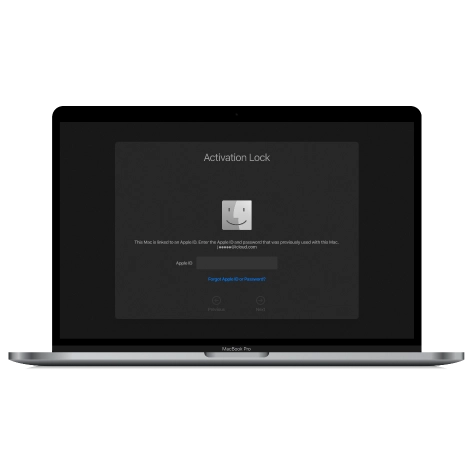
MacOS Activation Lock Bypass Tool
Price from $89.00
If your MacBook, iMac, Mac Mini, or Mac Pro is based on the INTEL T2 Chip, you can utilize the CheckM8 software to bypass the Find My Mac and remove the MacOS iCloud Activation Lock screen
Discover SoftwarePrice from $99.00
-

EFI Firmware Passcode Unlock Tool
Price from$99.00
A fast and effective solution to unlock the EFI security firmware (BIOS) password protection on any Mac equipped with the T2 chip is available
Discover SoftwarePrice from $99.00
-
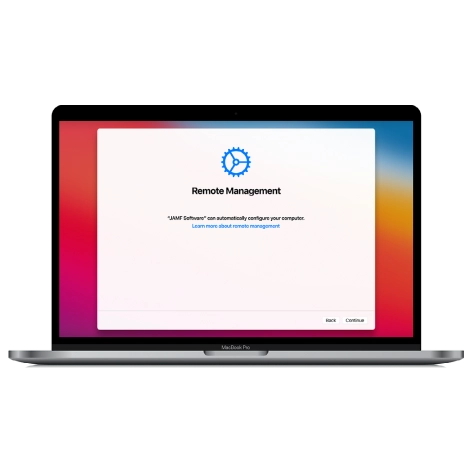
MacOS Remote Management Bypass Tool
Price from$29.00
This tool is designed to bypass remote management on MacOS, allowing you to gain full access to your MacBook without any restrictions imposed by the MDM lock screen.
Discover SoftwarePrice from $29.99
-

MDM Unlocking Tool [T2 INTEL]
Price from$79.00
The new CheckM8 software provides a permanent MDM unlock solution for MacBook Pro, Air, and other Mac computers that are equipped with T2 processors.
Discover SoftwarePrice from $79.99
-
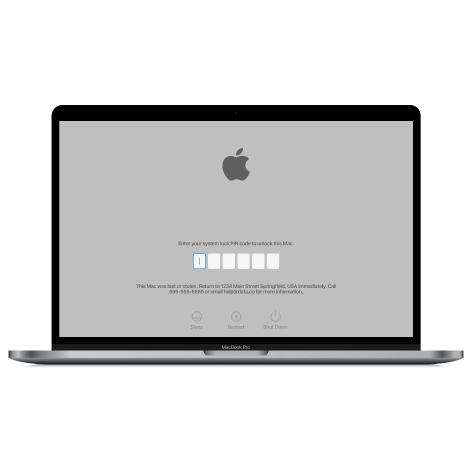
MacOS iCloud PIN Lock Bypass Tool
Price from$49.00
If you're having trouble with the iCloud PIN lock screen or have forgotten your PIN, this software can help you bypass the lock screen and regain access to your Intel-based MacBook
Discover SoftwarePrice from $49.00
information-center
-
Secure
Your personal info will always be protected and never be exposed
-
Customer Support
We take pride in providing excellent customer support services
-
Free Updates
You will have lifetime access to free software updates.
-
Money-Back Guarantee
We guarantee a 100% money-back policy.

 Ukrainian / UK
Ukrainian / UK
 Arabic / AR
Arabic / AR
 Spain / ES
Spain / ES
 Deutsch / DE
Deutsch / DE
 Italy / IT
Italy / IT
 zh / ZH
zh / ZH
 French / FR
French / FR
 Russian / RU
Russian / RU

