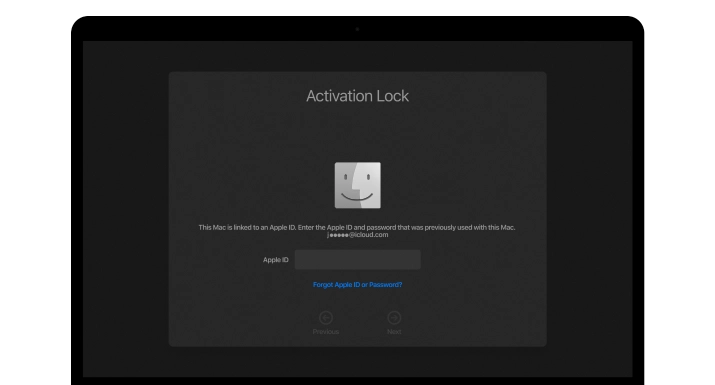
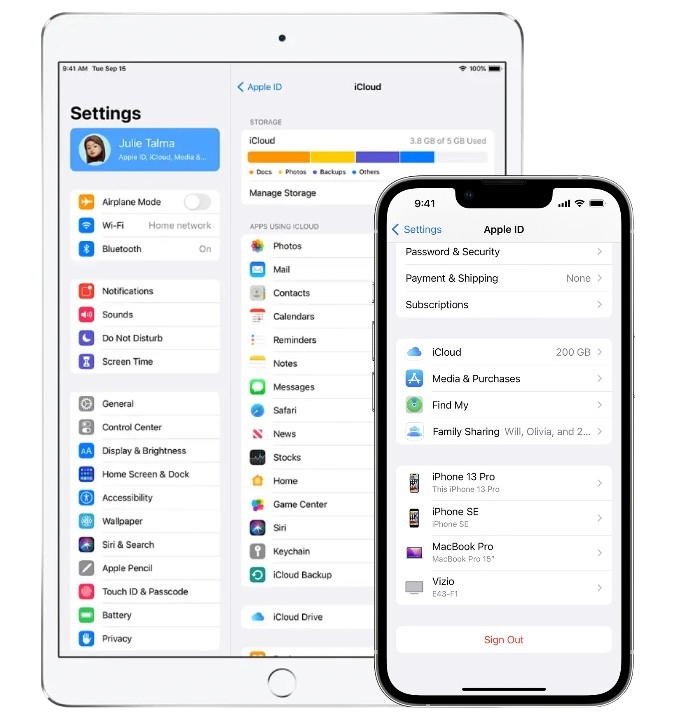
Find My Mac
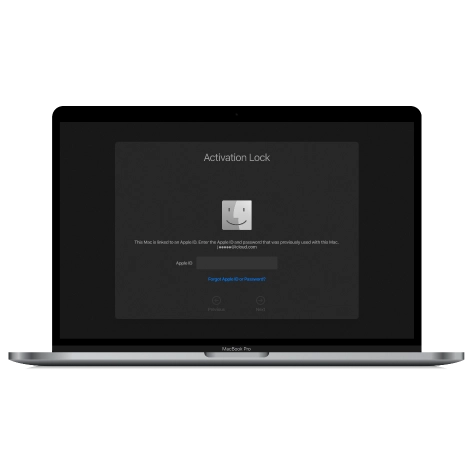
Activation Lock
Bypass Tool.
The CheckM8 Dev Team has developed software that is capable of bypassing the Activation Lock on Mac computers that have an Apple T2 security chip and are powered by INTEL CPUs.
COMPATIBLE WITH:
-
- MacBook Pro
- MacBook Air
- Mac Mini
- iMac
- Mac Pro
- that use an Intel-based Apple T2 chip
-
- macOS Sierra
- macOS High Sierra
- macOS Mojave
- macOS Catalina
- macOS Big Sur
- macOS Monterey
- macOS Ventura
- macOS Sonoma
- macOS Sequoia
- Support is available for any Bridge OS version!
-
- The software is compatible with macOS 10.11 or later
VIDEO PRESENTATION
Remove iCloud Activation Lock on Macbook
Find My Mac Activation Lock Screen Removal
The CheckM8 software has the ability to bypass the Mac Activation Lock, which can be very helpful if you're unable to reset your Apple ID or passcode with Apple's assistance. If you're struggling to remember your Apple ID password, there's no need to panic because CheckM8 can remotely bypass the Mac Activation lock screen for you!
There are several advantages to using the CheckM8 software. To begin with, it can be used on any Mac device that has the T2 security chip, which is designed to prevent unauthorized startups. Additionally, the software does not require an Apple ID or password to successfully bypass the Mac Activation Lock.
After iCloud is bypassed on Mac computers, the Activation Lock screen on the device is skipped, resulting in the device appearing as if it was never locked.
Our development team has put in a lot of effort to create a simple and quick software that can remove the Activation Lock from your MacOS device with just one click. The software also includes built-in instructions that can assist you in removing the macOS activation lock without any issues.
The CheckM8 software has been designed to be extremely user-friendly, which means you don't need any technical skills or knowledge to use it.
Download Find My Mac Activation Lock Bypass Tool.
RECENT SOFTWARE RELEASES
Software Updates.
Discover the most recent updates for the CheckM8 FMM Activation Lock Bypass Tool. Would you like to be the first to receive information on new updates and discounts?
JOIN TELEGRAM🗓 Devices verified before August 20, 2024 can still use Signal Bypass only
CheckM8 Reviews
How to remove iCloud Activation Lock on MacBook Pro, MacBook Air, Mac Mini, iMac using CheckM8 Tool
PLEASE NOTE:
Bypassing the Find My Mac Activation Lock involves using the CheckM8 exploit, a bootrom exploit, to skip the iCloud activation step on locked computers. This allows you to use the device without any restrictions, except for when you factory reset or reinstall macOS. If that happens, you'll need to use the tool again to skip the activation lock. Don't worry, though, the re-bypass process is always free! Please note that this only skips the activation step on the device, not the activation server.
-
Step 1.
Download & Install Software
Please download the latest version of the CheckM8 FMM Activation Lock Bypass tool for macOS and install it on a working Mac computer.
The following are the requirements for using the CheckM8 FMM Bypass Software:
1. A Mac computer that is activation locked and needs to be made workable.
2. Another working Mac computer where you can install the CheckM8 software.
3. A USB type C to USB type C cable to connect the two computers.
CHECKM8.PKG' CAN'T BE OPENED
Please keep in mind that if you try to launch an app from an identified developer that is not registered with Apple, a warning message may appear. However, this does not necessarily mean that there is anything wrong with the app.
Once the installation process is complete, you can open the CheckM8 app on your Mac using Launchpad.
Step 2.
Verify if the device is eligible
Use a USB Type-C to USB Type-C cable to connect the locked macOS device to the working Mac. Please ensure that you select the correct port!

The software will detect the locked Mac and prompt you to enter the device into DFU mode. You will receive a detailed onscreen guide on how to do this.
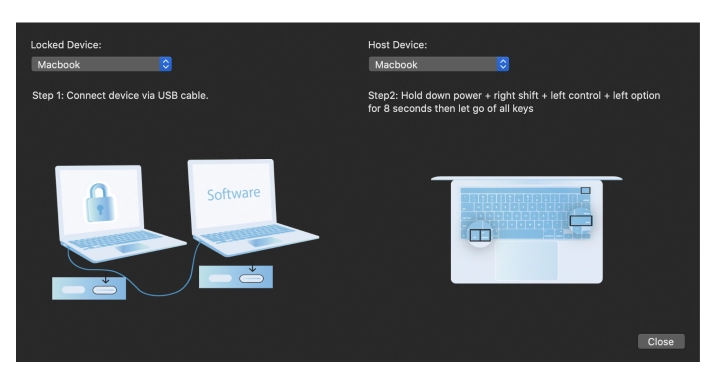
Follow the onscreen instructions carefully, or you can use guides:

How to put your Mac into DFU mode
Once the Mac is in DFU mode, CheckM8 will automatically identify it and run a verification to ensure that it can bypass the Activation Lock on your device. If your device is supported, you will receive a notification and a proposal to order a software license.
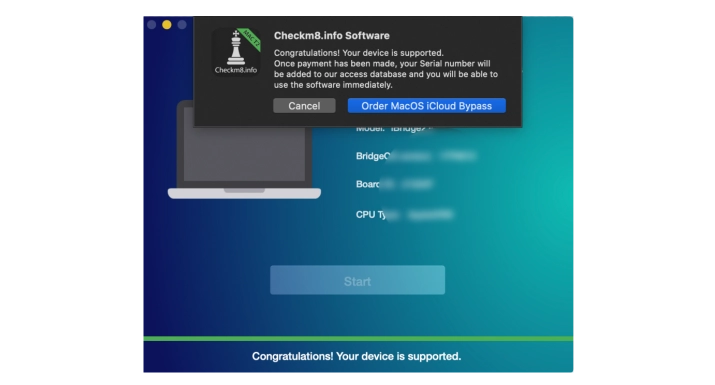
Step 3.
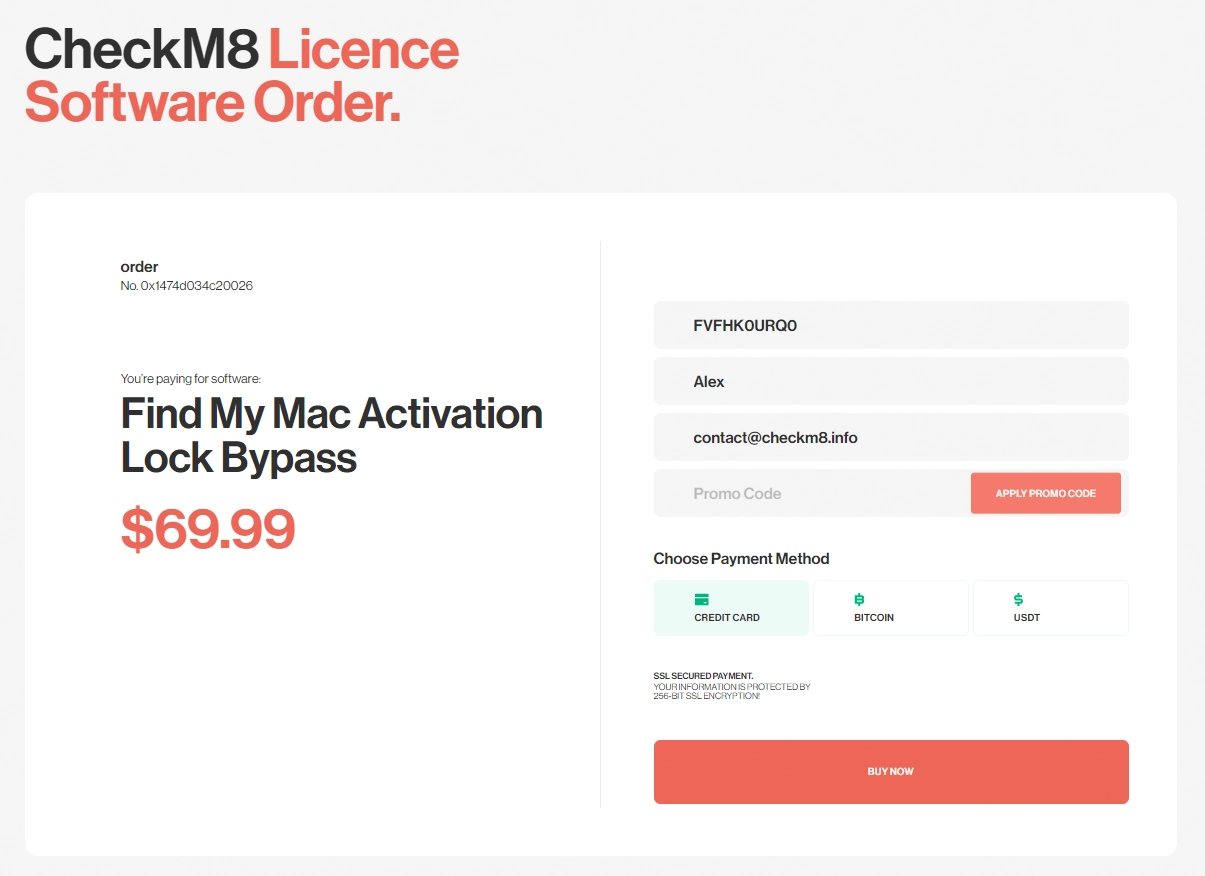
Order Service
After making the payment for your order, the CheckM8 database will record your Mac's serial number, which will grant you a lifetime license to reuse the software at no extra cost, provided that the activation lock returns and a new version of macOS is supported by the software.
Step 4.
Bypass Find My Mac
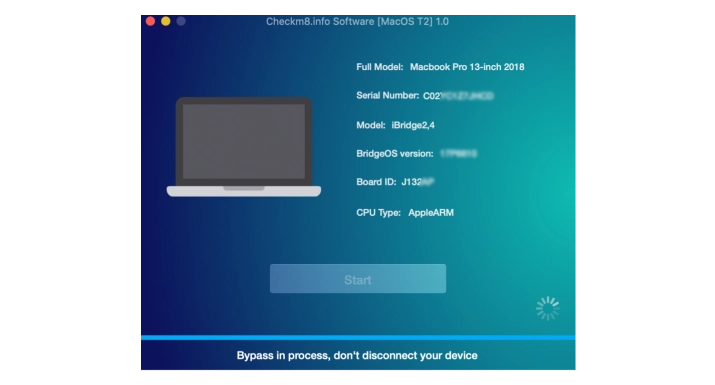
Upon successful payment, the software will detect the license for the serial number of the iCloud-locked Mac and prompt you to start the Activation Lock bypass process. Press the Start button on CheckM8 and be patient while the software works. It will notify you of the success as soon as the bypass process is completed.
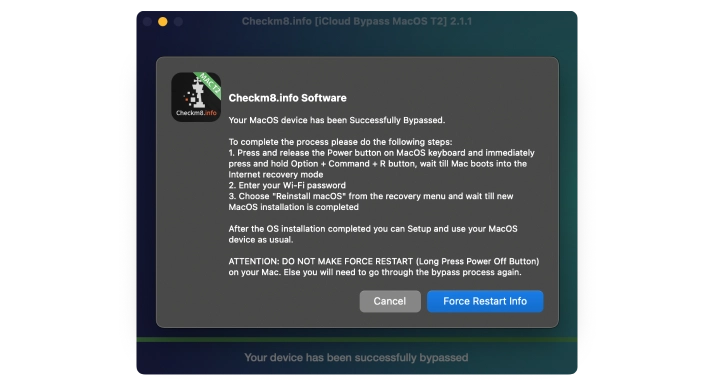
After successfully bypassing the Find My Mac feature on your locked device, the Mac will turn off. Press the Power button to turn on the Mac and start using it without any restrictions or limitations. You can now use your Apple ID, download any software, and enjoy the full functionality of your device.
FMM BYPASS
Find My Mac Activation Lock Removal Service
Prices.
Please check the list of Mac computer models that are supported, as well as the associated pricing, for removing the activation lock screen using the checkm8 software with just one click.
-
-
MacBook Pro
A2251, A2289, A1989, A1790, A2159, A2141, A1790, A1989
$50
-
-
-
MacBook Air
A1932
$50
-
-
-
Mac Mini
A1793
$50
-
-
-
iMac
A1793
$50
-
-
-
iMac Pro
A1862
$50
-
-
-
iMac 4K
A2116
$50
-
-
-
iMac 5K
A2115
$50
-
-
-
Mac Pro
A1791, A2304
$50
-
Tools for unlocking iPhone and iPad.
-
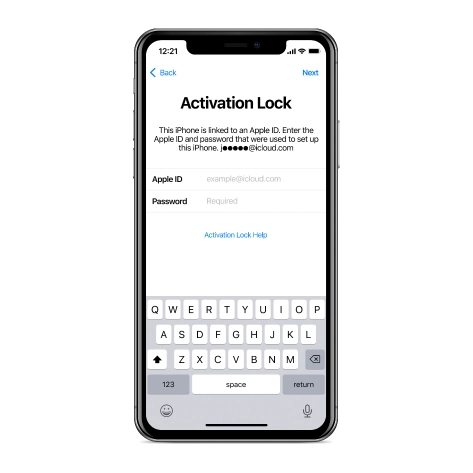
iCloud Activation Lock Removal Tool
Price from $15.99
This tool is used to get rid of the iCloud Activation Lock from iPhone and iPad devices running on iOS up to version 18
Discover SoftwarePrice from $15.99
-
![Remote Management [MDM] Bypass Tool](https://checkm8.info/new/img/service/remote-management-iphone-unlock.webp)
Remote Management [MDM] Bypass Tool
Price from $44.99
This software allows you to bypass the Mobile Device Management (MDM) Configuration Profile and remove the MDM lock screen on any iPhone and iPad model
Discover SoftwarePrice from $44.99
-
Open Menu FMI iCloud Unlock
From $14.99
This tool is made for iPhones and iPads that are not stuck on the Activation Lock screen, but instead are fully working devices with access to Media & Purchases menu
Discover SoftwarePrice from $14.99
Tools for unlocking Mac Computers.
-
MacOS Activation Lock Bypass Tool
Price from $89.00
If your MacBook, iMac, Mac Mini, or Mac Pro is based on the INTEL T2 Chip, you can utilize the CheckM8 software to bypass the Find My Mac and remove the MacOS iCloud Activation Lock screen
Discover SoftwarePrice from $99.00
-

EFI Firmware Passcode Unlock Tool
Price from$99.00
A fast and effective solution to unlock the EFI security firmware (BIOS) password protection on any Mac equipped with the T2 chip is available
Discover SoftwarePrice from $99.00
-
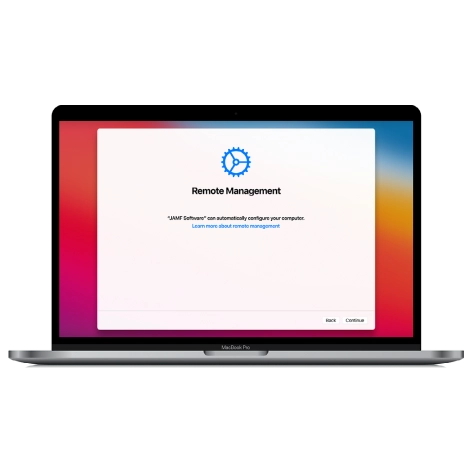
MacOS Remote Management Bypass Tool
Price from$29.00
This tool is designed to bypass remote management on MacOS, allowing you to gain full access to your MacBook without any restrictions imposed by the MDM lock screen.
Discover SoftwarePrice from $29.99
-

MDM Unlocking Tool [T2 INTEL]
Price from$79.00
The new CheckM8 software provides a permanent MDM unlock solution for MacBook Pro, Air, and other Mac computers that are equipped with T2 processors.
Discover SoftwarePrice from $79.99
-
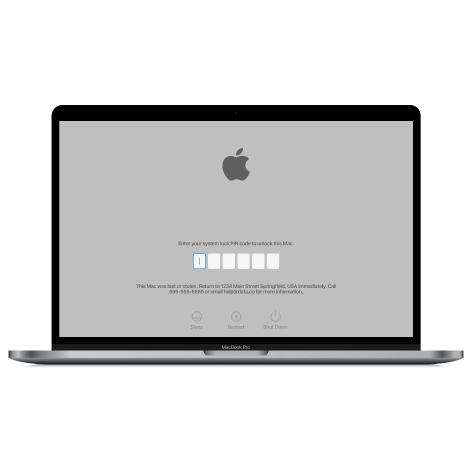
MacOS iCloud PIN Lock Bypass Tool
Price from$49.00
If you're having trouble with the iCloud PIN lock screen or have forgotten your PIN, this software can help you bypass the lock screen and regain access to your Intel-based MacBook
Discover SoftwarePrice from $49.00
information-center
-
Secure
Your personal info will always be protected and never be exposed
-
Customer Support
We take pride in providing excellent customer support services
-
Free Updates
You will have lifetime access to free software updates.
-
Money-Back Guarantee
We guarantee a 100% money-back policy.

 Ukrainian / UK
Ukrainian / UK
 Arabic / AR
Arabic / AR
 Spain / ES
Spain / ES
 Deutsch / DE
Deutsch / DE
 Italy / IT
Italy / IT
 zh / ZH
zh / ZH
 French / FR
French / FR
 Russian / RU
Russian / RU

